The concept of botnets has been a growing concern in the cybersecurity community for years. These networks of compromised devices, often referred to as "zombies," can be controlled remotely by attackers to conduct malicious activities, such as distributed denial-of-service (DDoS) attacks, phishing campaigns, and data theft. To form a botnet, several key components are required, and understanding these components is crucial for developing effective countermeasures.

The Anatomy of a Botnet
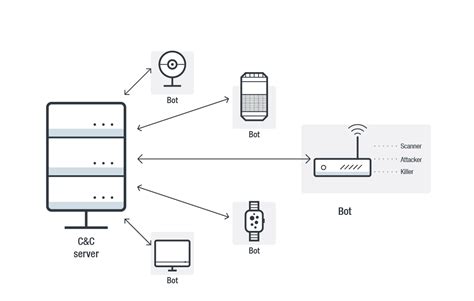
A botnet typically consists of three primary components: the command and control (C2) server, the botmaster, and the compromised devices or bots.
Command and Control (C2) Server
The C2 server is the central hub of the botnet, responsible for communicating with the compromised devices and issuing commands. This server is usually a compromised machine or a dedicated server hosted on a compromised network. The C2 server can be located anywhere in the world, making it challenging to track and take down.
How C2 Servers Communicate with Bots
C2 servers use various communication protocols to interact with the compromised devices, including:
- HTTP/HTTPS: Hypertext Transfer Protocol (HTTP) and Hypertext Transfer Protocol Secure (HTTPS) are commonly used protocols for communication between the C2 server and the bots.
- DNS: Domain Name System (DNS) tunneling is another method used by botnets to communicate with the C2 server.
- P2P: Peer-to-Peer (P2P) protocols, such as BitTorrent, can be used by botnets to communicate with each other and the C2 server.
Botmaster
The botmaster is the individual or group responsible for creating, managing, and controlling the botnet. They use the C2 server to issue commands to the compromised devices, which then carry out the desired malicious activities.
Compromised Devices or Bots
Compromised devices, also known as bots or zombies, are the machines that have been infected with malware and are under the control of the botmaster. These devices can include:
- Computers: Desktops, laptops, and mobile devices can all be compromised and become part of a botnet.
- IoT Devices: Internet of Things (IoT) devices, such as smart home appliances and cameras, are increasingly being targeted by attackers to form botnets.
- Servers: Compromised servers can also be used as bots to conduct malicious activities.
How Devices Become Compromised
Devices can become compromised through various means, including:
- Malware: Malicious software, such as viruses, Trojans, and ransomware, can infect devices and allow them to be controlled by the botmaster.
- Phishing: Phishing attacks can trick users into installing malware or providing login credentials, which can then be used to compromise devices.
- Vulnerabilities: Unpatched vulnerabilities in software or operating systems can be exploited by attackers to gain control of devices.

The Role of C2 Servers in Botnet Formation
C2 servers play a crucial role in botnet formation, as they provide the infrastructure for the botmaster to communicate with the compromised devices. The C2 server is responsible for:
- Command and control: The C2 server issues commands to the compromised devices, which then carry out the desired malicious activities.
- Data exfiltration: The C2 server can be used to exfiltrate data from the compromised devices, such as login credentials, credit card numbers, and other sensitive information.
- Malware updates: The C2 server can be used to update the malware on the compromised devices, ensuring that the botnet remains active and effective.
Challenges in Taking Down Botnets
Taking down botnets can be a challenging task, as they often involve a large number of compromised devices spread across different geographic locations. Some of the challenges in taking down botnets include:
- Identifying the C2 server: Locating the C2 server can be difficult, as it may be hosted on a compromised network or a dedicated server.
- Disrupting communication: Disrupting communication between the C2 server and the compromised devices can be challenging, as botnets often use multiple communication protocols and channels.
- Removing malware: Removing malware from compromised devices can be a time-consuming process, especially if the malware is sophisticated and has a low detection rate.

Conclusion
In conclusion, forming a botnet requires several key components, including the command and control server, the botmaster, and the compromised devices or bots. Understanding these components is crucial for developing effective countermeasures to prevent and take down botnets. By disrupting communication between the C2 server and the compromised devices, removing malware from infected devices, and identifying and taking down the C2 server, it is possible to disrupt and dismantle botnets.
Recommendations
To prevent botnets, it is essential to:
- Keep software and operating systems up to date with the latest security patches.
- Use antivirus software and a firewall to protect against malware and unauthorized access.
- Use strong passwords and enable two-factor authentication to prevent unauthorized access to devices and networks.
- Monitor network traffic and device activity for suspicious behavior.
- Educate users about phishing attacks and other social engineering tactics used by attackers.
Call to Action
We encourage readers to share their experiences and insights on botnets and cybersecurity in the comments section below. Additionally, we invite readers to share this article on social media to raise awareness about the importance of cybersecurity and the threats posed by botnets.
What is a botnet?
+A botnet is a network of compromised devices that can be controlled remotely by an attacker to conduct malicious activities.
How do devices become compromised?
+Devices can become compromised through malware, phishing attacks, and unpatched vulnerabilities in software or operating systems.
What is the role of the C2 server in a botnet?
+The C2 server is responsible for communicating with the compromised devices, issuing commands, and exfiltrating data.