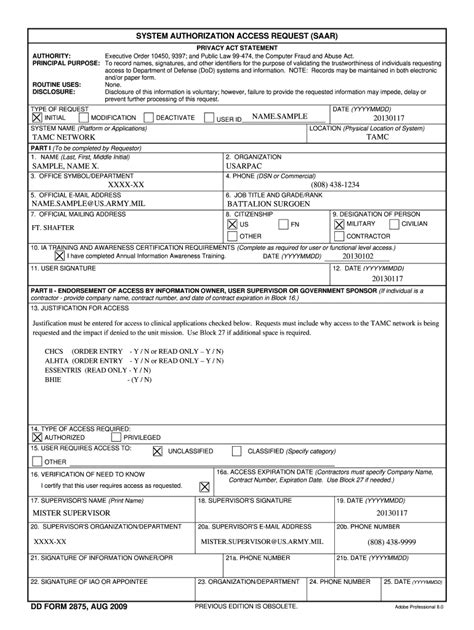
The DD Form 2875, also known as the "System Authorization Access Request (SAAR)" form, is a crucial document used by the United States Army to grant access to its computer systems and networks. The form is used to request authorization for individuals to access specific systems, and it requires detailed information about the requester, the system, and the level of access being requested.
Filling out the DD Form 2875 efficiently is essential to ensure that access requests are processed quickly and accurately. In this article, we will discuss five ways to fill out the DD Form 2875 efficiently, including understanding the form's requirements, gathering necessary information, using online resources, avoiding common mistakes, and submitting the form correctly.
Understanding the Form's Requirements

Before filling out the DD Form 2875, it is essential to understand the form's requirements. The form consists of several sections, including the requester's information, system information, access level, and authorization. Each section requires specific information, and understanding what is required can help you fill out the form efficiently.
The requester's information section requires details such as name, rank, and organization. The system information section requires details about the system being accessed, including the system name, location, and purpose. The access level section requires details about the level of access being requested, including the type of access, duration, and justification.
Sections of the DD Form 2875
- Section 1: Requester's Information
- Section 2: System Information
- Section 3: Access Level
- Section 4: Authorization
Gathering Necessary Information

Gathering necessary information before filling out the DD Form 2875 can save time and reduce errors. Ensure you have all the required information, including the requester's information, system information, and access level details.
It is also essential to review the form's instructions and any additional guidance provided by the Army. Understanding the form's requirements and gathering necessary information can help you fill out the form efficiently.
Tips for Gathering Information
- Review the form's instructions and guidance
- Gather all required information before filling out the form
- Verify information with the requester and system owner
Using Online Resources

The Army provides online resources to help fill out the DD Form 2875 efficiently. The Army's website offers guidance, instructions, and templates to assist with filling out the form.
Using online resources can help you understand the form's requirements, gather necessary information, and avoid common mistakes. Additionally, online resources can provide examples of completed forms, which can be helpful in understanding the form's layout and content.
Online Resources
- Army's website:
- Army's cybersecurity website:
- DD Form 2875 template:
Avoiding Common Mistakes

Common mistakes can delay the processing of the DD Form 2875. Avoiding common mistakes, such as incomplete information, incorrect formatting, and lack of authorization, can help ensure that the form is processed efficiently.
It is essential to review the form carefully before submitting it to ensure that all information is complete and accurate. Additionally, using online resources and templates can help avoid common mistakes.
Common Mistakes to Avoid
- Incomplete information
- Incorrect formatting
- Lack of authorization
- Incorrect system information
Submitting the Form Correctly

Submitting the DD Form 2875 correctly is essential to ensure that it is processed efficiently. The form should be submitted to the designated authority, which is usually the system owner or the cybersecurity office.
Ensure that the form is complete, accurate, and signed by the authorized personnel. Additionally, follow any specific submission guidelines provided by the Army.
Submission Guidelines
- Submit the form to the designated authority
- Ensure the form is complete, accurate, and signed
- Follow specific submission guidelines provided by the Army
By following these five ways to fill out the DD Form 2875 efficiently, you can ensure that access requests are processed quickly and accurately. Remember to understand the form's requirements, gather necessary information, use online resources, avoid common mistakes, and submit the form correctly.
If you have any questions or need further guidance, please comment below or share this article with others who may find it helpful.
What is the purpose of the DD Form 2875?
+The DD Form 2875 is used to request authorization for individuals to access specific Army computer systems and networks.
What information is required on the DD Form 2875?
+The form requires information about the requester, system, access level, and authorization.
Where can I find guidance on filling out the DD Form 2875?
+Guidance can be found on the Army's website, cybersecurity website, and by contacting the system owner or cybersecurity office.