Wireless security is a top concern for individuals and organizations alike, as the number of Wi-Fi enabled devices continues to grow. Two popular security protocols, WPA2 and WEP, are often compared when discussing wireless security. However, one of these protocols stands out as the stronger security option.
Understanding WEP and WPA2

Before diving into the comparison, it's essential to understand what WEP and WPA2 are. WEP (Wired Equivalent Privacy) is an older security protocol that was introduced in 1997 as part of the IEEE 802.11 standard. Its primary goal was to provide a level of security equivalent to that of a wired network. However, WEP has been widely criticized for its vulnerabilities and weaknesses.
WPA2 (Wi-Fi Protected Access 2), on the other hand, is a more modern security protocol that was introduced in 2004. It was designed to address the security concerns of WEP and provide a more robust security solution. WPA2 is widely considered to be the stronger security option, but why?
The Limitations of WEP

WEP has several limitations that make it a less secure option. One of the primary concerns is its use of static keys, which can be easily compromised by hackers. Additionally, WEP uses a weak encryption algorithm, known as RC4, which has been widely criticized for its vulnerabilities.
Another limitation of WEP is its lack of authentication. WEP relies on a simple authentication process that can be easily bypassed by hackers. This makes it easy for unauthorized devices to connect to a WEP-secured network.
Weak Keys and Encryption
WEP's use of weak keys and encryption is a significant concern. The keys used in WEP are typically 40-bit or 104-bit, which can be easily cracked by hackers using brute-force attacks. Additionally, the encryption algorithm used in WEP is RC4, which has been shown to be vulnerable to attacks.
Lack of Authentication
WEP's lack of authentication is another significant concern. The authentication process used in WEP is simple and can be easily bypassed by hackers. This makes it easy for unauthorized devices to connect to a WEP-secured network.
The Strengths of WPA2

WPA2 is widely considered to be the stronger security option due to its several strengths. One of the primary advantages of WPA2 is its use of dynamic keys, which are more secure than the static keys used in WEP. Additionally, WPA2 uses a more robust encryption algorithm, known as AES, which is widely considered to be unbreakable.
Another advantage of WPA2 is its use of authentication. WPA2 uses a more secure authentication process that makes it difficult for unauthorized devices to connect to a WPA2-secured network.
Dynamic Keys and Encryption
WPA2's use of dynamic keys and encryption is a significant advantage. The keys used in WPA2 are typically 128-bit or 256-bit, which are much more secure than the keys used in WEP. Additionally, the encryption algorithm used in WPA2 is AES, which is widely considered to be unbreakable.
Secure Authentication
WPA2's use of authentication is another significant advantage. The authentication process used in WPA2 is more secure than the process used in WEP, making it difficult for unauthorized devices to connect to a WPA2-secured network.
Why WPA2 is the Stronger Security Option

Based on the limitations of WEP and the strengths of WPA2, it's clear that WPA2 is the stronger security option. WPA2's use of dynamic keys, robust encryption, and secure authentication make it a more secure choice for wireless networks.
In addition to its technical advantages, WPA2 is also widely supported by most devices, making it a more practical choice for wireless networks. Whether you're setting up a home network or a business network, WPA2 is the better choice for security.
Best Practices for WPA2 Security

While WPA2 is a more secure option than WEP, there are still best practices to follow to ensure the security of your wireless network.
Use a Strong Password
One of the most important best practices is to use a strong password. A strong password should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and special characters.
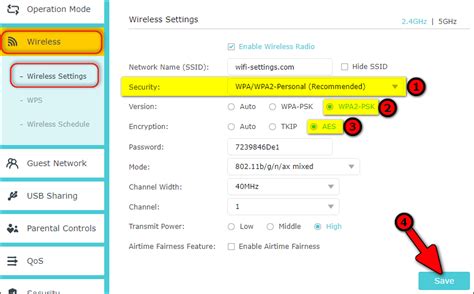
Use WPA2 with AES
Another best practice is to use WPA2 with AES encryption. AES is widely considered to be unbreakable, making it the most secure encryption algorithm available.
Use a Secure Authentication Method
Using a secure authentication method, such as WPA2-PSK (Pre-Shared Key), is also important. This method uses a pre-shared key to authenticate devices, making it more secure than other authentication methods.
Conclusion

In conclusion, WPA2 is the stronger security option for wireless networks. Its use of dynamic keys, robust encryption, and secure authentication make it a more secure choice than WEP. By following best practices, such as using a strong password and secure authentication method, you can ensure the security of your wireless network.
We hope this article has provided you with valuable information on wireless security protocols. Share your thoughts and comments below!
What is WEP?
+WEP (Wired Equivalent Privacy) is an older security protocol that was introduced in 1997 as part of the IEEE 802.11 standard. Its primary goal was to provide a level of security equivalent to that of a wired network.
What is WPA2?
+WPA2 (Wi-Fi Protected Access 2) is a more modern security protocol that was introduced in 2004. It was designed to address the security concerns of WEP and provide a more robust security solution.
Why is WPA2 more secure than WEP?
+WPA2 is more secure than WEP due to its use of dynamic keys, robust encryption, and secure authentication. WPA2's encryption algorithm, AES, is widely considered to be unbreakable, making it a more secure choice than WEP.