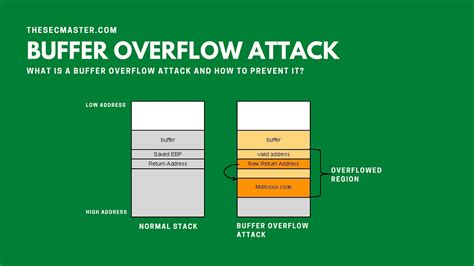
Buffer overflow is a type of attack that occurs when a program tries to store more data in a buffer (a region of memory used to temporarily hold data) than it is designed to hold. This can cause the extra data to spill over into adjacent areas of memory, potentially allowing an attacker to execute malicious code.
The importance of understanding buffer overflow attacks cannot be overstated. As technology advances and more devices become connected to the internet, the potential for buffer overflow attacks grows exponentially. In fact, according to a report by OWASP, buffer overflow is one of the top 10 most common web application security risks.
In this article, we will delve into the world of buffer overflow attacks, exploring what they are, how they work, and what can be done to prevent them. We will also look at some real-world examples of buffer overflow attacks and discuss the impact they can have on individuals and organizations.
What is a Buffer Overflow Attack?

A buffer overflow attack occurs when a program attempts to write more data to a buffer than it is designed to hold. This can happen in a variety of ways, such as when a user inputs more data than expected or when a program receives more data from a network connection than it is designed to handle.
When a buffer overflow occurs, the extra data can spill over into adjacent areas of memory, potentially allowing an attacker to execute malicious code. This can lead to a range of problems, including:
- Crashing the program: A buffer overflow can cause a program to crash or become unstable, leading to a denial of service (DoS) attack.
- Executing malicious code: An attacker can use a buffer overflow to execute malicious code, potentially allowing them to gain control of the system or steal sensitive data.
- Gaining elevated privileges: A buffer overflow can be used to gain elevated privileges, allowing an attacker to access sensitive areas of the system.
Types of Buffer Overflow Attacks
There are several types of buffer overflow attacks, including:
- Stack-based buffer overflow: This type of attack occurs when a buffer overflow occurs on the stack, allowing an attacker to execute malicious code.
- Heap-based buffer overflow: This type of attack occurs when a buffer overflow occurs on the heap, potentially allowing an attacker to execute malicious code.
- Integer overflow: This type of attack occurs when an integer value is incremented beyond its maximum limit, potentially allowing an attacker to execute malicious code.
How Do Buffer Overflow Attacks Work?

A buffer overflow attack typically involves the following steps:
- Identifying a vulnerability: An attacker identifies a vulnerability in a program that can be exploited to cause a buffer overflow.
- Crafting malicious input: The attacker crafts malicious input that is designed to cause a buffer overflow.
- Sending the malicious input: The attacker sends the malicious input to the program, potentially causing a buffer overflow.
- Executing malicious code: If the buffer overflow is successful, the attacker can execute malicious code, potentially gaining control of the system or stealing sensitive data.
Real-World Examples of Buffer Overflow Attacks
Buffer overflow attacks have been used in a range of high-profile attacks, including:
- The Morris Worm: In 1988, a buffer overflow attack was used to spread the Morris Worm, a computer worm that infected thousands of computers.
- The Code Red Worm: In 2001, a buffer overflow attack was used to spread the Code Red Worm, a computer worm that infected hundreds of thousands of computers.
- The Heartbleed Bug: In 2014, a buffer overflow attack was used to exploit the Heartbleed Bug, a vulnerability in the OpenSSL encryption library.
Preventing Buffer Overflow Attacks

Preventing buffer overflow attacks requires a combination of good coding practices and security measures. Some of the ways to prevent buffer overflow attacks include:
- Using secure coding practices: Developers can use secure coding practices, such as bounds checking and input validation, to prevent buffer overflow attacks.
- Implementing security measures: Organizations can implement security measures, such as firewalls and intrusion detection systems, to prevent buffer overflow attacks.
- Keeping software up-to-date: Keeping software up-to-date can help to prevent buffer overflow attacks by ensuring that any known vulnerabilities are patched.
Best Practices for Preventing Buffer Overflow Attacks
Some of the best practices for preventing buffer overflow attacks include:
- Using secure coding practices: Developers should use secure coding practices, such as bounds checking and input validation, to prevent buffer overflow attacks.
- Implementing security measures: Organizations should implement security measures, such as firewalls and intrusion detection systems, to prevent buffer overflow attacks.
- Keeping software up-to-date: Organizations should keep software up-to-date to ensure that any known vulnerabilities are patched.
In conclusion, buffer overflow attacks are a serious security risk that can have significant consequences for individuals and organizations. By understanding how buffer overflow attacks work and taking steps to prevent them, we can help to protect ourselves and our organizations from these types of attacks.
We hope this article has provided you with a comprehensive understanding of buffer overflow attacks and how to prevent them. If you have any questions or comments, please don't hesitate to reach out.
What is a buffer overflow attack?
+A buffer overflow attack is a type of attack that occurs when a program tries to store more data in a buffer (a region of memory used to temporarily hold data) than it is designed to hold.
How do buffer overflow attacks work?
+A buffer overflow attack typically involves identifying a vulnerability in a program, crafting malicious input, sending the malicious input to the program, and executing malicious code.
How can I prevent buffer overflow attacks?
+You can prevent buffer overflow attacks by using secure coding practices, implementing security measures, and keeping software up-to-date.